Windows Mobile Application Security Testing - Part 1
In this article series we will learn about the tool and technique required to perform WP application security assessment. Also we’ll create Window mobile application testing environment to perform security assessment on WP applications.
Introduction: Windows phone
Windows Phone is a proprietary smartphone operating system developed by Microsoft. It is the successor to Windows Mobile, although it is incompatible with the earlier platform. With Windows Phone, Microsoft created a new user interface, featuring a design language named "Modern" (which was formerly known as "Metro"). Unlike its predecessor, it is primarily aimed at the consumer market rather than the enterprise market. It was first launched in October 2010 with Windows Phone 7.
Windows Phone 8
WP8 runs ARM hardware architecture, similar to iOS, Android, and Blackberry. WP8 migrated to the Windows NT kernel instead of Windows CE which WP7 used. WP8 also uses the Windows Phone Runtime application architecture, not identical to WinRT, to allow developers convergence between Windows 8 and WP8. Applications for WP8 may be coded in .NET (C# or VB.NET) and C++ but not JavaScript.
WP8 being Windows NT kernel based allows for multiple benefits from a end user security perspective. These security controls do not help a tester but do help make the device more secure and attractive to enterprise users and decision makers.
- 128-bit BitLocker for full disk encryption
- NTFS file system
- Sandboxed apps – no access to other apps
- SafeBoot: Secure boot with Unified Extensible Firmware Interface (EUFI)
- This makes it difficult for software without correct digital signature to be loaded on your Windows Phone. Something jailbreakers will need to bypass. More on the jailbreaking later.
- TPM 2.0 standard, requires unique keys to be burned into the chip during production
- All Windows Phone 8 binaries must have legit digital signatures from Microsoft to run
New Security Features in Windows Phone 8.1
Microsoft added some security features in WP 8.1 to secure users. A Windows Phone 8.1 mobile device is malware resistant as it uses the same technologies that are used by Windows 8.1 desktop operating system. It secures the boot process, specifically UEFI and its Secure Boot component. UEFI Secure Boot verifies that the boot loader is trusted, and then Trusted Boot protects the rest of the startup process by verifying that all Windows boot components have integrity and can be trusted. If any malware has modified any file, Trusted Boot prevents such files from launching. Unsigned apps not from the Windows Store, are unable to run on Windows Phone.
- Secured enrollment with MDM systems
- Security policy management
- Lock down the phone to a specified set of applications and settings (Assigned Access)
- Automatically initiate VPN connections (auto-triggered VPN)
- Remote Assistance
- Remote business data removal
- Encryption of apps and confidential organizational data on removable storage
- Support for Secure and Multipurpose Internet Mail Extensions
- Support for enterprise Wi-Fi connectivity
- Support for virtual smart cards
- Support for new virtual private network (VPN) tunnel types.
Digital Right Management (DRM)
Microsoft signing all app in order to run into Locked device (non-developer unlocked) it’s similar to apple requires that code have a signed a binary for it to run non-jailbroken iOS device.
Windows Phone 8 all app are obtained via the windows phone store. Microsoft defined all application submitted to the store are subject to Microsoft defined submission process before being accepted and code signed with a certificate issued by the aptly named Certification Authority, Microsoft Marketplace CA. Signed apps are then made available for purchase or free download to the general public who own Windows Phone 8 devices. In addition to being codesigned, applications from the Store are protected using the FairPlay DRM technology. Tampering with the XAP or APPX files being installed results in the installation being halted.
All applications have to be Microsoft signed to run on WP8 or 8.1 devices. When developer mode is unlocked on a device, applications can be sideloaded, but in the context of Store applications running on the device of a standard consumer, all apps must be signed. We will learn about sideloading later.
Application Sandboxing
Windows phone 8.x closed architecture and applications are sandboxed to control their access to system resources to prevent them from accessing other application data. In windows phone 8.x all third-party applications from the store run in AppContainers.
AppContainer
AppContainer provides high level process-isolation mechanism which offers security permissions check in operating system resources such as file, registry and other resources. Windows phone 8.x all application run inside an appContainer and check app can be only its own private file sandbox. If application wants to read write outside of it, including other application data its fail.
Capabilities
Capabilities is to ability of application to access OS services such as camera or networking which controls by that app capabilities. Capabilities are also used to provision the security of the least privilege chamber (LPC) and reduce the attack surface by only provisioning ACLs for what the application requires. Applications should only be assigned capabilities which they require to perform their functionality and any unused capabilities removed.
ID_CAP_NETWORKING—Outbound and inbound network access ID_CAP_PHONEDIALER—Access to the dialer functionality ID_CAP_MICROPHONE—Access to the microphone API ID_CAP_LOCATION—Access to geolocation data ID_CAP_ISV_CAMERA—Access to device’s built-in camera
<Capabilities> <Capability Name="ID_CAP_NETWORKING" /> <Capability Name="ID_CAP_WEBBROWSERCOMPONENT" /> <Capability Name="ID_CAP_CONTACTS" /> <Capability Name="ID_CAP_PHONEDIALER" /></Capabilities>Capability elements are entries in the manifest file that notify the user while installing the app of special software capabilities that your app receives.
If you want to check more capability and its function you can check this in Microsoft site.
Prerequisites
- Windows 8 OS
- Physical Device or Emulator
- Windows Phone SDK 8.0 (You can download from here http://download.microsoft.com/download/9/3/8/938A5074-461F-4E3D-89F4-5CE2F42C1E36/wpsdkv80_enu1.iso)
Setup Environment for Windows Mobile Applications testing
Windows 8 OS
For test environment its required windows 8 OS because of windows phone SDK supports only on windows 8 Operating system.
We also need the following system requirement for the windows application testing lab.
System requirements:
In the BIOS, the following features must be supported:
- Hardware-assisted virtualization.
- Second Level Address Translation (SLAT).
- Hardware-based Data Execution Prevention (DEP).
- 4 GB or more of RAM.
- 64-bit version of Windows 8 Pro edition or higher. Network requirements:
- DHCP.
- Automatically configured DNS and gateway settings.
- In Windows, Hyper-V must be enabled and running.
- You have to be a member of the local Hyper-V Administrators group.
Windows Phone SDK tool
Windows SDK tool is the core tool for development and security assessment on windows 8.x. SDK tool included two of the most important tools are included one is Visual Studio and another is the emulator. Both tool you can use for reviewing code and running apps from source respectively.
Visual studio is Microsoft official integrated development environment and its used for development of WP applications.
You can use Visual Studio in you security assessment for
- Manually reviewing source code
- Running project from source on an emulator and devices
- You can use for debugging tools on source code.
Windows SDK installation
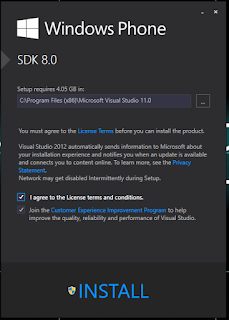
Download and install windows phone SDK 8 in your system. WP 8 SDK provides you with the tools that you use to development and deploy application in device. Also it’s useful for further analysis.
You can download windows sdk as .iso format which can be write the image file to blank DVD or use mount the image file virtual as DVD devices like DAEMON Tools lite.
Windows phone Developer unlocked Device (non-Jailbroken Device)
Microsoft has provided feature to developers, sideload apps in device for debugging and testing purpose. You can unlock your device by registering your phone with windows developer phone registration which will provide you to sideload your developer signed app for testing purpose. Only the limitation of unlocked device that you can only install maximum 3 developer signed apps.
We can use Developer unlocked device to sideload developer signed app and use for further WP application security analysis.
To unlock the device you must should install SDK and by using developer phone registration you can successfully unlock your device.
Registering your phone:
To register a phone, use the Windows Phone Developer Registration tool. This is a stand-alone tool that’s installed as part of the Windows Phone SDK.
Turn on your phone and unlock the phone screen.

On your phone ensure the date and time should correct.
Connect your phone by using USB cable.
On your system search app “Windows Phone Developer Registration” in start screen
In case unable to find the app then you can also use this path to locate the developer registration app: C:\Program Files (x86)\Microsoft SDKs\Windows Phone\v8.0\Tools\Phone Registration\PhoneReg.exe
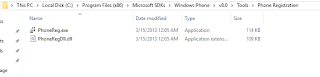
Run the app PhoneReg.exe
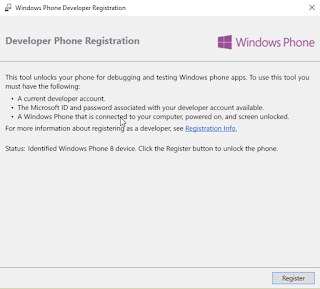
Ensure that your phone should be unlocked the phone screen.
Now click on the register and provide your any Hotmail or Microsoft account. (If you do not have Microsoft account, recommend you to register account in Hotmail)
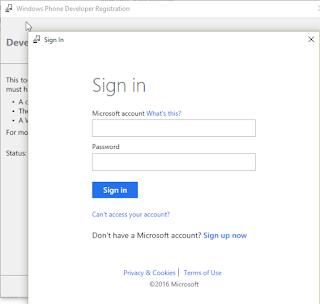
Congratulation!!! You have successfully registered your device and unlocked your device.
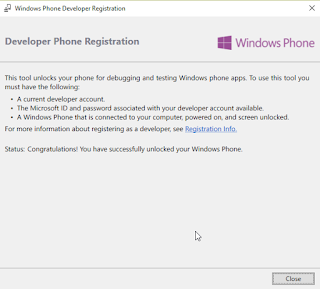
Now you can now able to sideload apps (only dev signed app) in your device.
Conclusion:
In this article we learned Windows Phone application security basics and setup the environment. Next article we learn about application files and how we’ll sideload the app and which tools we need for deploy the developer signed applications.
Reference:
https://msdn.microsoft.com/library/windows/apps/jj206936(v=vs.105).aspx